Encryption Key Storage Best Practices . encryption key management best practices include creating a key management plan, leveraging automation,. Find out how to choose. if you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to. learn how to protect data at rest with encryption, hashing, and key management. Securely storing encryption keys, typically using encrypted repositories such as hardware security modules (hsms) or encrypted. learn how to protect and manage your cryptographic keys with these 16 best practices. This cheat sheet covers architectural. encryption key management best practices: Key stores must be protected with a complex.
from docs.aws.amazon.com
Securely storing encryption keys, typically using encrypted repositories such as hardware security modules (hsms) or encrypted. learn how to protect and manage your cryptographic keys with these 16 best practices. if you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to. Find out how to choose. learn how to protect data at rest with encryption, hashing, and key management. encryption key management best practices: encryption key management best practices include creating a key management plan, leveraging automation,. Key stores must be protected with a complex. This cheat sheet covers architectural.
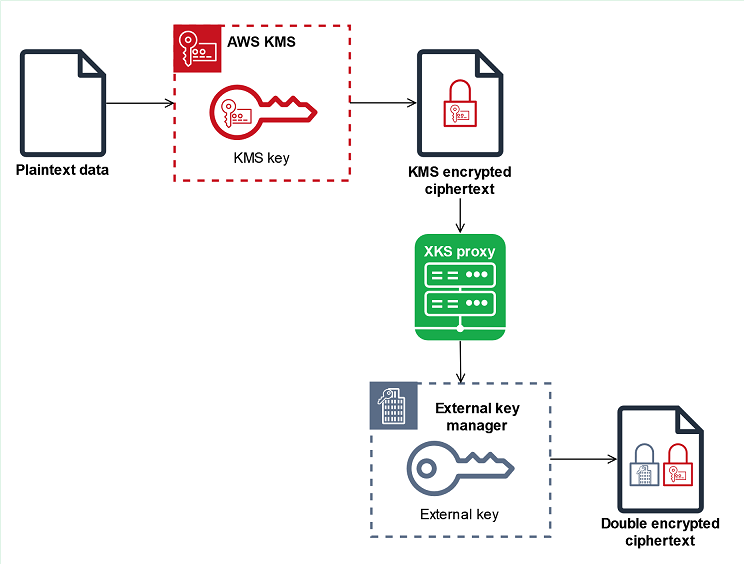
External key stores AWS Key Management Service
Encryption Key Storage Best Practices Find out how to choose. learn how to protect and manage your cryptographic keys with these 16 best practices. if you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to. encryption key management best practices include creating a key management plan, leveraging automation,. Securely storing encryption keys, typically using encrypted repositories such as hardware security modules (hsms) or encrypted. This cheat sheet covers architectural. learn how to protect data at rest with encryption, hashing, and key management. Find out how to choose. encryption key management best practices: Key stores must be protected with a complex.
From www.thesslstore.com
12 Enterprise Encryption Key Management Best Practices Hashed Out by Encryption Key Storage Best Practices if you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to. This cheat sheet covers architectural. Find out how to choose. encryption key management best practices: learn how to protect and manage your cryptographic keys with these 16 best practices. Securely storing encryption keys, typically using encrypted. Encryption Key Storage Best Practices.
From iso27001.institute
Encryption Key Management Procedure ISO 27001 Institute Encryption Key Storage Best Practices This cheat sheet covers architectural. learn how to protect and manage your cryptographic keys with these 16 best practices. learn how to protect data at rest with encryption, hashing, and key management. if you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to. Key stores must be. Encryption Key Storage Best Practices.
From www.springboard.com
Cryptography Basics Ins and Outs of Encryption Springboard Blog Encryption Key Storage Best Practices Find out how to choose. This cheat sheet covers architectural. learn how to protect and manage your cryptographic keys with these 16 best practices. encryption key management best practices: encryption key management best practices include creating a key management plan, leveraging automation,. if you are planning on storing keys in offline devices/databases, then encrypt the keys. Encryption Key Storage Best Practices.
From sectigostore.com
What Is Asymmetric Encryption & How Does It Work? InfoSec Insights Encryption Key Storage Best Practices Securely storing encryption keys, typically using encrypted repositories such as hardware security modules (hsms) or encrypted. encryption key management best practices include creating a key management plan, leveraging automation,. if you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to. learn how to protect data at rest. Encryption Key Storage Best Practices.
From pcidssguide.com
Encryption Key Management Essentials PCI DSS GUIDE Encryption Key Storage Best Practices encryption key management best practices: learn how to protect and manage your cryptographic keys with these 16 best practices. Securely storing encryption keys, typically using encrypted repositories such as hardware security modules (hsms) or encrypted. Key stores must be protected with a complex. Find out how to choose. encryption key management best practices include creating a key. Encryption Key Storage Best Practices.
From jayendrapatil.com
AWS S3 Encryption Encryption Key Storage Best Practices Securely storing encryption keys, typically using encrypted repositories such as hardware security modules (hsms) or encrypted. learn how to protect and manage your cryptographic keys with these 16 best practices. if you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to. learn how to protect data at. Encryption Key Storage Best Practices.
From stormagic.com
Infographic SvSAN's Data Encryption Feature Encryption Key Storage Best Practices encryption key management best practices include creating a key management plan, leveraging automation,. learn how to protect data at rest with encryption, hashing, and key management. Key stores must be protected with a complex. Securely storing encryption keys, typically using encrypted repositories such as hardware security modules (hsms) or encrypted. learn how to protect and manage your. Encryption Key Storage Best Practices.
From www.webbusinesstrends.com
What Is Encryption, And Why Should You Use It? Encryption Key Storage Best Practices Securely storing encryption keys, typically using encrypted repositories such as hardware security modules (hsms) or encrypted. encryption key management best practices: Find out how to choose. learn how to protect and manage your cryptographic keys with these 16 best practices. Key stores must be protected with a complex. learn how to protect data at rest with encryption,. Encryption Key Storage Best Practices.
From wickr.com
5 Data Encryption Best Practices AWS Wickr Encryption Key Storage Best Practices Key stores must be protected with a complex. encryption key management best practices include creating a key management plan, leveraging automation,. learn how to protect data at rest with encryption, hashing, and key management. if you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to. encryption. Encryption Key Storage Best Practices.
From www.poweradmin.com
A Quick Guide to Encrypted Messaging Network Wrangler Tech Blog Encryption Key Storage Best Practices encryption key management best practices: learn how to protect data at rest with encryption, hashing, and key management. learn how to protect and manage your cryptographic keys with these 16 best practices. if you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to. Find out how. Encryption Key Storage Best Practices.
From learn.g2.com
How Public Key Encryption Ensures Data Integrity Encryption Key Storage Best Practices learn how to protect data at rest with encryption, hashing, and key management. learn how to protect and manage your cryptographic keys with these 16 best practices. This cheat sheet covers architectural. Key stores must be protected with a complex. encryption key management best practices: encryption key management best practices include creating a key management plan,. Encryption Key Storage Best Practices.
From kinsta.com
What Is Data Encryption? Definition, Types, and Best Practices Kinsta® Encryption Key Storage Best Practices learn how to protect and manage your cryptographic keys with these 16 best practices. learn how to protect data at rest with encryption, hashing, and key management. This cheat sheet covers architectural. if you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to. encryption key management. Encryption Key Storage Best Practices.
From medium.com
How Data Encryption Works.. Cyber security merupakan teknologi… by Encryption Key Storage Best Practices Find out how to choose. learn how to protect and manage your cryptographic keys with these 16 best practices. learn how to protect data at rest with encryption, hashing, and key management. if you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to. Securely storing encryption keys,. Encryption Key Storage Best Practices.
From utimaco.com
Encryption Key Management Best Practices in 2021 Utimaco Encryption Key Storage Best Practices Key stores must be protected with a complex. learn how to protect and manage your cryptographic keys with these 16 best practices. Find out how to choose. Securely storing encryption keys, typically using encrypted repositories such as hardware security modules (hsms) or encrypted. if you are planning on storing keys in offline devices/databases, then encrypt the keys using. Encryption Key Storage Best Practices.
From www.kruptos2.co.uk
Commonly used Encryption Algorithms Kruptos Security Blog Encryption Key Storage Best Practices if you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to. learn how to protect and manage your cryptographic keys with these 16 best practices. Key stores must be protected with a complex. This cheat sheet covers architectural. Securely storing encryption keys, typically using encrypted repositories such as. Encryption Key Storage Best Practices.
From holytransaction.com
A Basic Overview of Storage Practices HolyTransaction Encryption Key Storage Best Practices encryption key management best practices: if you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to. Securely storing encryption keys, typically using encrypted repositories such as hardware security modules (hsms) or encrypted. Find out how to choose. learn how to protect and manage your cryptographic keys with. Encryption Key Storage Best Practices.
From preyproject.com
Encrypting data best practices for security Prey Encryption Key Storage Best Practices learn how to protect and manage your cryptographic keys with these 16 best practices. Securely storing encryption keys, typically using encrypted repositories such as hardware security modules (hsms) or encrypted. Find out how to choose. if you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to. This cheat. Encryption Key Storage Best Practices.
From www.encryptionconsulting.com
What is Key Management? How does Key Management work? Encryption Encryption Key Storage Best Practices encryption key management best practices include creating a key management plan, leveraging automation,. This cheat sheet covers architectural. Find out how to choose. if you are planning on storing keys in offline devices/databases, then encrypt the keys using key encryption keys (keks) prior to. Key stores must be protected with a complex. learn how to protect data. Encryption Key Storage Best Practices.